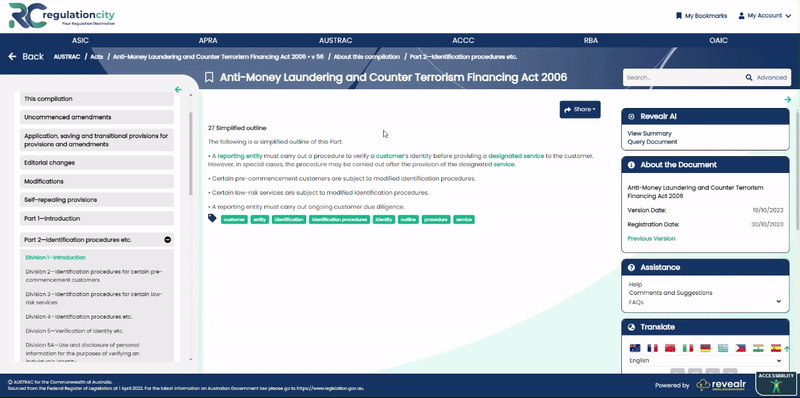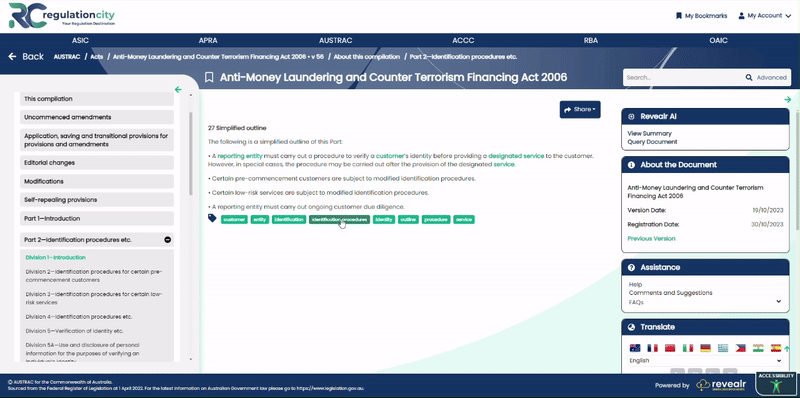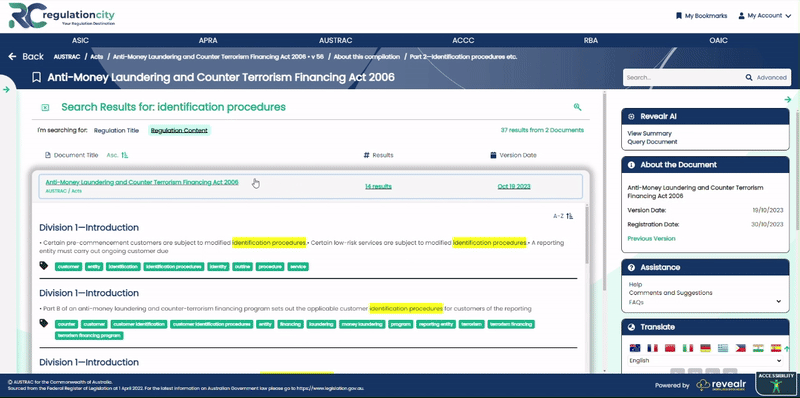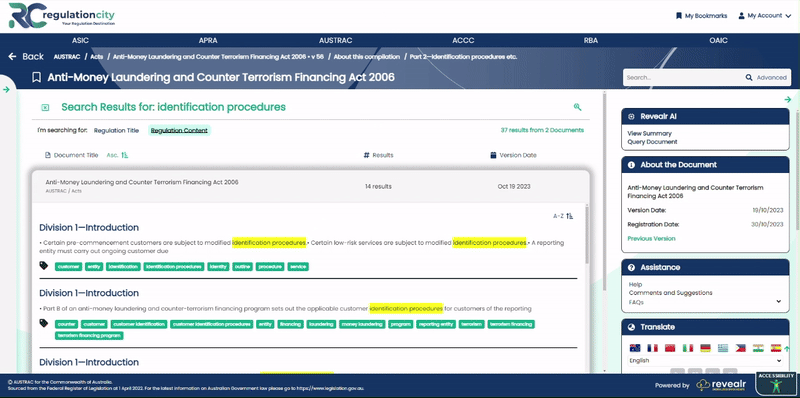
In the May Market Integrity Update, ASIC addresses a critical element of cyber security – the importance of mitigating third-party cyber attacks. It is no longer sufficient for organisations to enhance their internal cybersecurity – third party exposures must also be addressed.
ASIC is encouraging organisations to proactively identify critical vendors and pose three key questions:
- What level of access do third parties have to your systems?
Implement the principle of least privilege to minimise the impact of breaches. - How is third-party access protected?
Enable multi-factor authentication and closely monitor third-party credentials to reduce the risk of exploitation. - Where is your data?
Understand where sensitive data is stored, especially by third-party providers, to ensure appropriate protection. If you lack control over data protection, assess the potential impact and consider reducing the amount of sensitive data shared.
The Office of the Australian Information Commissioner has developed a guide to securing personal information, including information held by third party providers.
Read ASIC’s update here.